The Five Pillars of Rail Communications Network Cybersecurity
Nokia’s Network Infrastructure Transportation Market Leader, Benoît Leridon, outlines a five-pillar strategy for securing your railway communications network.
Digitalisation is transforming rail networks, but unfortunately cyber threats are evolving just as quickly. While we’ve seen digitalisation transform rail operations, systems and infrastructure, the growth in data produced and transferred through communications networks opens them up to new risks.
One threat comes from denial-of-service (DoS) attacks. Another could be physical attacks on infrastructure like those that took place just before the Paris Olympics opening ceremony, through to more sophisticated cyberattacks such as those orchestrated on Poland’s national railway that brought 20 trains to a standstill.
Digitalisation has introduced new risks by creating a larger attack surface. An increasing number of applications, such as signalling and asset monitoring now depend on the communications network like never before, as multi-service networks seamlessly connect critical systems. Furthermore, infrastructure managers and rail operators may be hampered by legacy infrastructure challenges, as many older systems lack the necessary modern cybersecurity protections.
Add in global regulatory inconsistencies that further complicate security efforts, and you begin to see the significant challenges involved in securing a rail communications network.
Ensuring Your Rail Communications Network is Secure
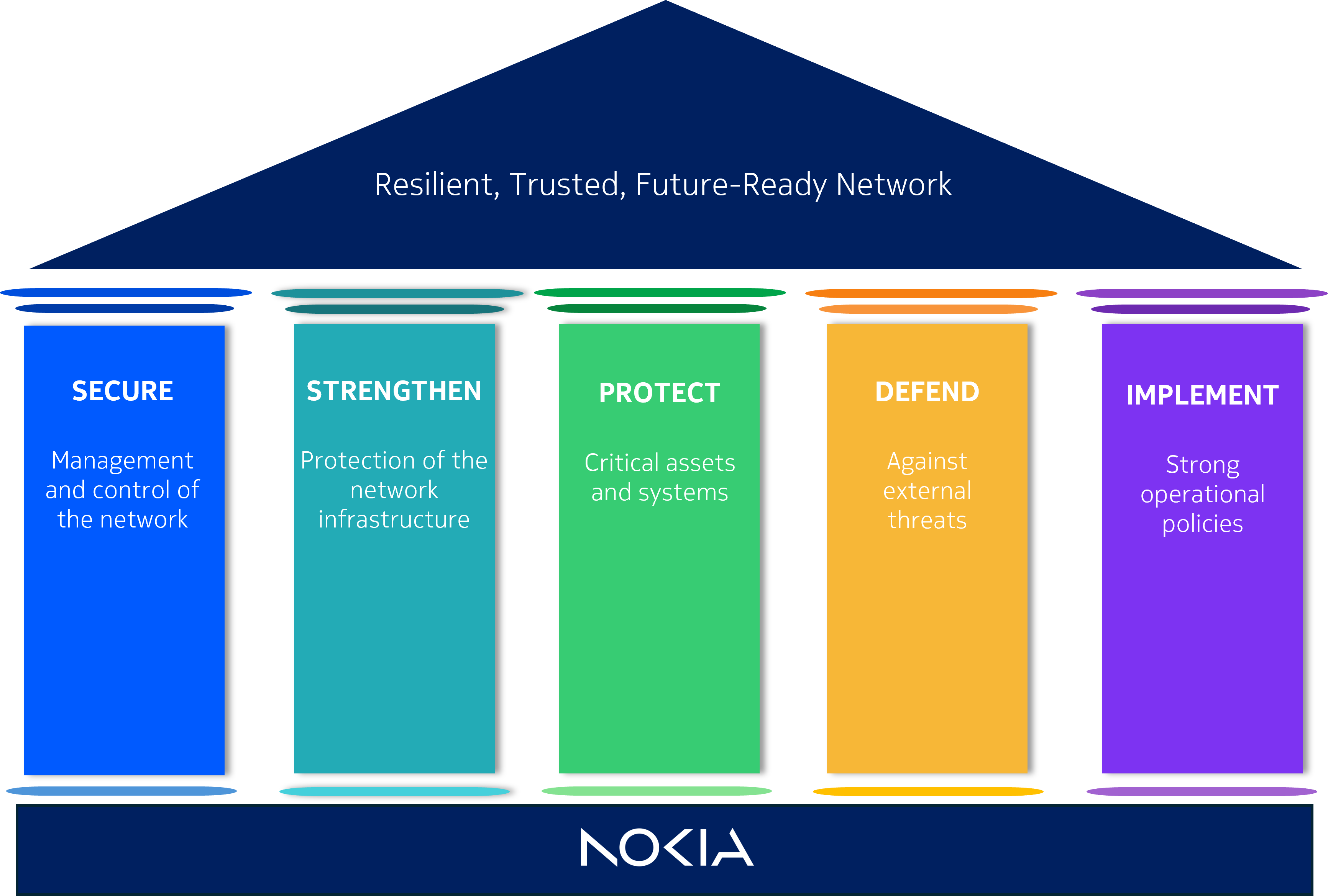
Nokia’s approach to securing railway communications networks is built around five pillars that address key security gaps and exposure points, ensuring resilience against evolving threats.
Pillar 1 – Securing Network Management Systems
Firstly, how do you protect the management of the network? Management interfaces can be a major vulnerability because, if breached, attackers gain full network control. Therefore, measures must be taken to ensure they remain secure.
This pillar covers role-based management, secured management protocols and management of security, with best practices including implementing multi-factor authentication (MFA), encryption and fine-grained, role-based management.
Pillar 2 – Strengthening Network Infrastructure Protection
Next up is securing the network (both digital and physical) itself, which is the first level of defence for your critical applications. This covers network availability, secured nodes, secured protocols and software quality. A critical infrastructure should consider a compliance with the common criteria (minimum EAL3+ level) for the multi service network components, to guarantee that the provider of the equipment has a development cycle that is fully controlled and makes security a priority.
Firewalls, network segmentation and automated threat detection help mitigate cyberattacks and secure multi-service networks. This in turn ensures applications such as signalling, based upon future railway mobile communication systems (FRMCS) or communication-based train control (CBTC), remain protected.
Pillar 3 – Protecting Critical Applications
Attackers target critical railway systems, from supervisory control and data acquisition (SCADA) to asset tracking. Therefore, pillar three should be about how you protect your applications – ensuring not only how you minimise the risk of an attack, but also the impact of an attack if it does happen.
Here, best practice should include multilayer and application-level encryption, redundancy, and physical protection. Zero-trust, including network access control, should be considered too.
The last can be particularly difficult to implement however, as there are potential points in a communications network where it may be difficult to set user access control. This can be due to device diversity in terms of age and operating system, which may mean that they can’t all use the latest authentication features.
Eventually all organisations will be able to set up zero trust access controls, but we’re looking at years. Given this fact, it’s important that all other security measures are implemented to ensure the impact of any cyberattack is limited.
Additionally, it’s strongly recommended to encrypt these applications. Regardless of whether they have built-in encryption capabilities, this can also be handled at the network level.
Pillar 4 – External Threats
It’s also important to consider protection from external threats. This is because although operational technology (OT) networks aren’t directly connected to the internet, they can still be vulnerable.
Therefore, they must be taken into account and firewalling, access controls and secure interconnection frameworks can help to reduce external risks.
Pillar 5 – Implementing Strong Operational Policies
It’s essential for infrastructure managers and rail operators to implement strong operational policies to ensure the security of their communications network.
Regular security audits, workforce training and real-time monitoring will further improve security posture, and compliance with NIS2 (in Europe), International Electrotechnical Commission (IEC) rail standards and Informational Sharing and Analysis Centre (ISAC) recommendations is essential.
NIS2 in particular offers a lot of guidance around operational policies and complying with its requirements will help to ensure the protection of your communications network.
Emerging Security Challenge
By following these five pillars of rail network cybersecurity infrastructure managers and rail operators are doing everything they can to secure their communications network today, but what of the future?
On a positive note, encryption is becoming a mandatory standard in railway networks, and we’re seeing more and more rail operators ask for this when upgrading their networks. However, the capabilities of quantum computing are rapidly developing and we hear talk of cybercriminals embracing the idea of ‘harvest now, decrypt later’ (HNDL); harvesting and storing encrypted data until quantum computing gives them the power to access this information.
Quantum threats aren’t immediate, and they’re likely to be a bigger issue for the banking sector than the rail industry. However, certain data and vulnerabilities could still be exploited so railways should take measures to protect against quantum threats.
With Nokia, quantum-safe encryption isn’t a future possibility – it’s available today. You can proactively safeguard your network with a future-ready solution, seamlessly integrating it into your existing encryption framework whenever you’re ready.
How Nokia Can Help You Secure Your Rail Communications Networks
As rail networks become more connected and digitalised, cyber threats are evolving and rail operators and infrastructure managers must take a proactive approach to network security to ensure safe, reliable and resilient operations.
A cybersecurity environment is only as strong as the software it depends on. Using a poorly designed or outdated firewall is like having a smoke alarm with dead batteries – it might be there, but it won’t protect you when it matters most. Ensuring up-to-date, robust defences is critical to safeguarding your network.
At Nokia, we provide end-to-end security solutions designed specifically for railway communications networks. Our multi-layered approach covers all five key pillars, and with decades of experience in railway communications technology, we deliver field-proven solutions that meet the highest security standards. Whether you’re upgrading legacy infrastructure or building the next-generation rail network, we have the expertise and technology to keep your operations secure now and ready for the digital era.
Find out how Nokia can help secure your railway network by visiting the Nokia Railways webpage.












