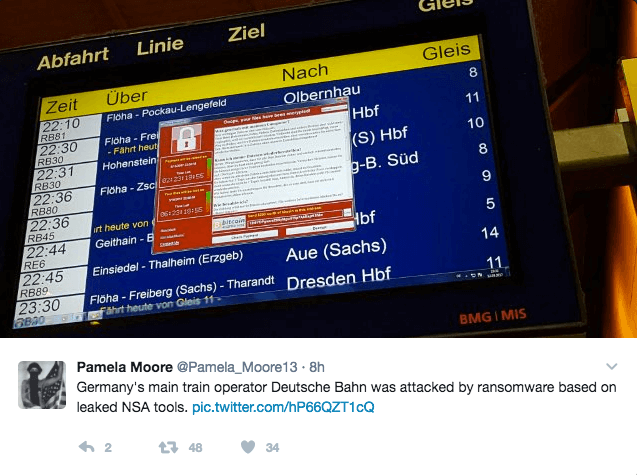
Why I Think Ransomware Is a Major Danger to the Rail Industry
If you didn’t already know, Swiss train manufacturer Stadler Rail suffered a data breach in early May 2020. The hacking gang demanded payment of a ransom of 6 million USD (5.8 million CHF) in bitcoin. “Stadler is not and has never been willing to make payments to blackmailers and has not entered into negotiations,” a spokesperson for the company told press agency AWP. When faced with the company’s refusal to negotiate, the hackers published some of the stolen documents on the internet. A cache of internal Stadler documents was shared via an anonymous Twitter message.
According to the message on the social network, accompanied by images, the perpetrators of the attack claim to have no less than 10,000 documents representing a data volume of 4 gigabits. The blackmailers gave Stadler a second chance to pay the ransom “before the publication of Part 2”.
According to the Tages-Anzeiger newspaper, the images published concern documents relating to loans and bank contracts as well as a tax agreement with the canton of Thurgau and a construction project in Altenrhein.
More Attacks, More Financial Losses
News stories like these are becoming increasingly common – proof that cyber-extortion is escalating and it’s very, very real. With attacks involving some of the world’s most nefarious ransomware – including Mase, Sodinokibi, DoppelPaymer, Nemty, Nefilim, CLOP and Sekhmet – victims of 2020’s biggest ransomware attacks spent at least 144 million USD on costs to June alone.⁵ Costs ranged from ransom payments to attack investigations, network rebuilds, backup restoring and protective measures against future attacks.
Over the past several years, ransomware has grown from a moderate risk to a major headline-grabbing menace. Attackers’ capabilities have developed over time. From the relatively ‘simple’ threat of data lockouts once synonymous with ransomware attacks, ransomware groups now pose even greater risks, and are developing ever more sophisticated ways to gain access to sensitive data, and even leak that data online. For example, in the first quarter of 2020, a number of prolific ransomware strains – including Sodinokibi, DoppelPaymer, Nemty, Nefilim, CLOP, and Sekhmet – led to the online publication of stolen data from non-paying victims.
Selling stolen data to competitors, using stolen data to attack victims’ business partners, or publicising victims’ ‘dirty secrets’ on the web for all to see are all increasingly common tactics. Attackers are also on the constant lookout for opportunities. With the rise of the COVID-19 pandemic, many attackers have taken advantage of victims’ search for information. By luring online users into opening malicious emails and attachments, these criminal groups have prayed on victims’ insecurities during a precarious time. Once users have fallen foul of phishing, they enable the attacker to steal their credentials. These credentials may give access to critical systems supporting our essential transport services and critical national infrastructure.
Operators of Essential Systems
Within train operating companies we have vital, critical systems on which performance depends. If we fail to plan, re-plan and reschedule in the face of unfavourable weather, vandalism, failed communications and operational technology, trains will be late, passengers will be angry and the economy as a whole is affected. It is bad for business and reputation and can lead to fines and penalties. The Office of Rail and Road has said it will penalise operating companies that fail to deliver when IT failure is a factor. It’s not just train planning and maintenance however, we have to roster staff, to make sure we have the correct people driving the trains, manning the platforms and managing the stations. Ticketing systems targeted will result in damaged revenue streams and passenger discomfort. Passenger information systems are important to the passenger experience and the movement of people across the stations, indeed the whole network. Connected to these are the HR systems and finance applications – once the hacker is into the network, critical systems are under threat. Advanced persistent threat (APT) attacks have delayed timelines, with attackers attempting to infect as many systems in a network as possible.
And then we have the trains themselves. Access via the passenger wifi to security systems such as CCTV and black box journey recorders could be exploited and end in major challenges to performance and safety. Proof that an attacker can make such invasions might be followed by a ransom demand or worse.
Financial Damage and Loss of Productivity
While statistics show that the U.S. faces the greatest threat from ransomware, no country nor any industry is safe. The following statistics have been recently published:
- 48% of UK organisations have been hit by ransomware in the last year
- 5.9 million GBP ransomware attacks were recorded in the UK in the first half of 2020
- 840,000 GBP is the average remediation cost of a successful ransomware attack to UK enterprises
Actually, there are additional unseen costs: damages due to lost productivity are usually 5–10x the actual ransom amount. And, today, almost anyone can contact a Ransomware-as-a-Service (RaaS) group to launch an attack.
The more the UK government goes head-to-head with Russia, the more state-sponsored terrorism will target UK critical national infrastructure. There is a double threat here – the nation will be targeted by both terrorists and criminal gangs with the same net result: delay, disruption and ultimately a threat to safety.
What Is Ransomware?
But just what is ransomware? In its simplest form, ransomware is malicious software that allows a hacker to restrict access to an individual’s or company’s vital information in some way, and then demand some form of payment to lift the restriction. The most common form of restriction is the encryption of important data on a computer or network, which essentially lets an attacker hold user data (or an entire system) hostage. Payment in cryptocurrency is the common demand, as the digital currency is both global and anonymous. Ransomware attacks are rapidly growing in popularity, and for good reason: with payments in the tens or hundreds of thousands of pounds, it’s an opportunity for criminals to make considerable sums.
It’s Been Going on Quite a While
Though it may seem like merely a decade-old idea, the notion of ransomware has been around for quite some time. In 1989, Dr Joseph Popp distributed a Trojan called PC Cyborg in which malware hid all folders and encrypt files on an infected PC’s C: drive. A script then delivered a ransom message demanding that 189 USD be directed to the PC Cyborg Corporation. The afflicted PC wouldn’t function until the ransom was paid and the malware’s actions were reversed. Since then, numerous enhancements to this type of scheme have been made, especially in the area of stronger file encryption. Now it’s virtually impossible for victims to decrypt their own files. Another type of ransomware scheme, dubbed ‘scareware’, displayed a warning on a user’s computer that the device was infected with malware that could be removed immediately by purchasing what turned out to be fake antivirus software. The scareware message appeared repeatedly, prompting many victims to purchase the ‘antivirus software’ just to get rid of the warning message.
The Attackers Include Boss and SpiderBoss – International Criminals
Today, the term ‘ransomware’ broadly describes a wide range of e-crime, malicious software programs, including DoppelMayer, REvil, Ethria, Netwalker and Maze. Each differs slightly in its tactics. For example, Maze not only encrypts the data on infected machines, but also siphons off copies of the originals, giving hackers extra leverage: failure to pay the ransom could result in confidential corporate data being leaked or sold online. Historically, the vast majority of attacks were against Windows-based systems. This is largely due to a numbers game; there are more Windows-based computers than any other type of OS. Yet now, Android and Mac ransomware attacks are on the rise, too and are only expected to grow.
In the early days of ransomware, attacks were largely opportunistic, affecting individual users’ or small businesses’ computers. Today, criminals are setting their sights on larger organisations with the resources to pay bigger ransom demands. These will include rail manufacturers, ROSCOs and train operating companies.
“Ransomware itself has become commoditised; literally anyone can contact a Ransomware as a Service (RaaS) group to deploy ransomware. Detecting potential ransomware attacks are and will be an increasingly critical part of enterprises in the future, as will the ability to respond quickly using automation.”
Damage from downtime can be as crippling, often costing 5 to 10 times the actual ransom amount when measured in lost productivity (slack labour and lost revenue opportunities).
Hope for the Best, Plan for the Worst!
They say there are five phases to a ransomware attack:
- Exploitation and infection
- Delivery and execution
- Backup spoliation
- File encryption
- User-notification, demands and if you are lucky…
What can rail companies do? Just hoping you won’t be attacked is not an option. Detection and prevention first and foremost – follow the guidelines given by NCSC in the Cyber Assurance Framework developed for the 2018 Network and Information Systems security regulations. Protective monitoring and anomaly detection are required by the NCSC framework, as are practised measures of recovery to reduce the damage done. Backing up your planning and rostering systems, and the files and records they rely on is not a bad idea either. Remember to use separate media or a third party. SIEM and SOC providers will advise on their products but I insist that prevention is KEY: while defence and monitoring may stop the attack, the attack chain cannot be activated if there are no vulnerabilities. If they can’t get past the first phase you are not going to suffer the fifth.
Governance
Operating companies need to put in place a hierarchy of governance to approve the measurement of risk and resulting expenditure on mitigation. This governance can oversee risk assessments of all IT systems, those on-board trains as well as those critical to performance, planning, rostering and maintenance. Signalling systems, used by TOCs but delivered by Network Rail, require collaboration. Connected systems, the compromise of which put operation at risk must be assessed and if necessary separated. Personnel controls such as vetting, training and the security awareness of staff are just as important as technical controls such as strong passwords and firewalls. Kill the vulnerabilities by patching and updating software, encrypting files at rest and in transit. Physical controls can be strengthened, and procedures refined to enhance technology and practice.
Professional Risk Analysts Required
Professional risk analysis and management will reduce vulnerabilities and the threat of compromise down to a reasonable level. In order to demonstrate to senior managers that the controls procured are proportionate, the risk manager must provide reports and documentation to prove the return on investment is appropriate. Risk management for IT systems has been taken seriously by central government and the armed forces for the last four decades. Now, as critical national infrastructure, the IT and communications networks supporting transport are being treated as precious assets and the operators of essential services are being charged with their security, it is time to develop risk assessment professionally. The dangers from hacking and particularly ransomware warrant an approach that will apply governance and resource to ensure no rail system is vulnerable to attack and all reasonable measures of defence are taken.
Confirming Your Worst Fears
It’s all very well identifying weaknesses in your systems because your controls don’t comply with the NCSC security framework. It is best to hold full and frank discussions, workshops if possible, with stakeholders for each system under review. Some IT systems can be subject to vulnerability scans. Central government and the armed forces use professional accredited penetration testing teams to provide a full IT health check. These will confirm (or otherwise) the security posture of your systems and with remedial action and continuous monitoring and improvement, give the necessary assurance to the stakeholders and those selected to provide governance.
By Joe Ferguson, NCSC Certified Cyber Practitioner and Senior Information Risk Analyst