By Joe Ferguson, NCSC Certified Cyber Practitioner and Senior Information Risk Analyst
As a lead consultant with IL7 Security, I have carried out risk assessments on IT for industry, banking, police, central government and defence for over two decades.
We have provided risk assessments for operational technology, mainly in transport, covering trains as well as planes, ships and even submarines. However, this has mainly involved analysis of the IT on those vehicles, not the traction or propulsion, and not with an emphasis on safety. It has been more about performance and confidentiality of information.
In 2018, IL7 were engaged as consultants in rail due to our knowledge of the NIS regulations, in particular the NCSC Cyber Assurance Framework. The contract also put me on the Thameslink Partnership Cyber Security Working Group, with Network Rail and Siemens as well as the Department for Transport and the NCSC. Representing both the train operator and IL7, I have often been asked “why is cyber security not part of safety risk assessment?” Recently a code of practice has sought to provide answers and to correct this anomaly.
A Much-Needed Code of Practice
This formidable code of practice comes from a combined NCSC and IET effort and will be published in the new year. It investigates the relationship between cyber security and safety. IL7 has been asked to provide a condensed overview for executive consumption. It goes without saying that performance and safety go together – if operational technology is not secure, it can be exploited, hacked or hi-jacked even; performance is impacted, and deterioration becomes a safety issue. Safety can very quickly become critically threatened. So why don’t we approach safety as a potential result of cyber failure? Why don’t we see cyber failure as a cause of danger, to performance and safety? We need to view them together and provide a full lifecycle approach to both security and safety. Information assurance, in government and defence address cyber as a constant hazard needing continual attention of senior management, buy-in from stakeholders, collaboration and continued assessment to maintain adequacy.
Key Ideas
- Safety and performance go together
- IT can facilitate safety and performance; compromised IT can endanger both
- If safety-related OT is note secure, it’s not safe
- Effective cyber security can require changes to safety systems
- Conflict between safety and security requires a business decision at the highest level
- Business decisions require an analysis of the issues, the risks involved, the implied costs, against the overall business opportunities
On-Board Information Technology
So, what do we mean by IT on the train? We know and rely on communications from Network Rail to provide signalling, movement authority, and interlocking. This can be wayside information, mobile radio to the driver or the train computer. On board the train, the driver and IT, whether it is ETCS, ERTMS or something less sophisticated, work together on deciding speed, accelerating, braking and when and which side to open the doors. How frustrating is it when IT doesn’t work? And then there’s the CCTV used for safety and the black box recorder without which the journey doesn’t happen. Add to this the passenger information system displays as well as the customer wifi and entertainment. All these can be connected together or separated by an air gap, connected to the wayside, or, dare I say, separated from each other, by sophisticated comms equipment, regularly tested, and monitored for intrusion as well as performance fault. Security protects systems from people (accidental or deliberate actions) – safety protects people from a system’s malfunctions.
Challenges
The code of practice recognises that there are challenges to overcome if we are to address cyber vulnerabilities that might become hazards. Not least is the fact that these disciplines have evolved differently. First of all, there is a perception that confidentiality impinges on availability – solutions and passwords need to be “open“. Excuses for not concentrating on the cyber threat have included the need to prioritise physical security and passenger safety from disease (thinking has understandably been put off by Covid) Both safety & cyber are represented at board level and differences can be ironed out by business decisions. The code of practice calls for common sense, collaboration, and trade-offs in negotiation where conflicts exist.
Compromise
One particular challenge is the fact that IT security risk assessments quite happily accept risk within a certain tolerance or appetite. Sometimes, when thinking of safety, we have zero tolerance – in IEC 62443 terms this is SIL 4 and like a radio block for movement authority needs an air gap. Most of the time IT systems cannot function with an air gap so there needs to be compromise. We need to address IT / cyber security in terms of “safe as far as reasonably preventable“. The issues are not ‘absolutes’ – business needs compromise – one without the other leads to failure.
Opportunities
The code of practice recognises there are many fundamental opportunities for conversation and businesses need to take these seriously. Safety looks at functional failure through weaknesses that exist throughout system lifecycles. Cyber security focuses on the attacker and changing opportunities to exploit weaknesses that dynamically change over time. We need to speak the same language and recognise the insider threat, the external threat, take into account the motivation and capabilities of serious attackers, not just the accidental system failure, the mechanical failure developed over time and ageing, or through minor, even casual, vandalism, weather related faults or acts of god.
Shared Principles
Appreciation of common sense and quality standards recognise that there are more shared principles than differences. Whether it is in accountability to the board of directors or compliance to recognised best practice and standards, people intuitively know what good looks like – they just need to channel this into a shared goal to provide service: service that provides performance and safety; service that avoids the pitfalls that a lack of cyber IQ will bring.
We need to develop these shared principles and apply the concept of adversaries if we want to explain an attack in cyber terms. If rail is under attack from cyber, we know cyber-attack has a recognised pattern. The code of practice doesn’t elaborate on this, but we can see that a cyber adversary has a sophisticated armoury and follows tried and tested procedures to infiltrate and compromise your IT and OT systems. That is why operators need to be prepared and have defences in place to recognise and deal with attacks in order to regain control and recover operational efficiency.
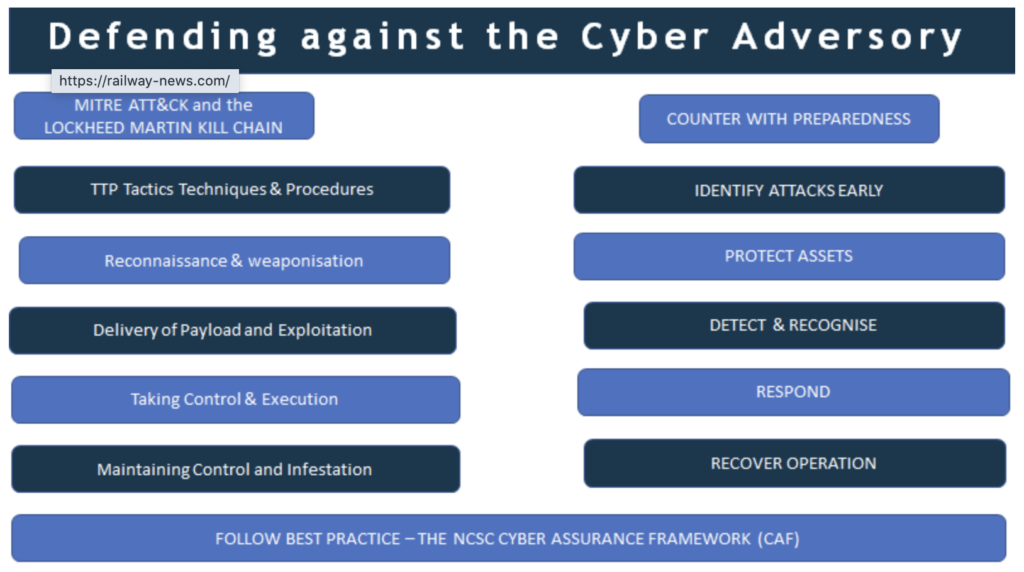
The NCSC’s NIS cyber security framework gives us excellent advice. Competent authorities such as the DfT are judging how well operators of essential service are progressing towards achieving all the outcomes required. These outcomes are for systems critical to the delivery of service – we should include the delivery of safe and efficient operating performance in our targets. The IEC/NCSC code of practice mirrors this ambition. The framework clearly sets out the objectives:
- To manage risk
- To defend our systems
- To detect attacks
- To minimise impact
Management & Accountability
In line with international standards such as ISO 27001, and the US NIST, the code of practice offers its own rules for engagement, best practice, compliance so to speak. From a management perspective, responsibility for cyber security and safety is a corporate gift, managed at the most senior level. The board fulfils legal obligations by laying down standards in policy that satisfy both safety and security requirements within a coherent management structure. It is important, though, that the whole organisation is given ownership and involved in reaching the achieved goals and unnecessary blame is not attributed when replacing faults, technical or procedural, with improvements. It is therefore necessary to deploy both safety and cyber experts, cross-pollinating knowledge to foster consensus and teamwork. Management must also ensure that responsibilities are cascaded down the supply chain whether third parties are responsible for delivery or maintenance of product or services.

Whichever system is under scrutiny, its scope, interconnecting dependencies, and business context should be documented. What it contributes to the business is its value, the impact if it is damaged. Then one should identify weaknesses and the interfaces that may allow an attack. Software in particular must be examined in scrutinising a safety system. The consequences of failure should allow you to judge how much risk management needs to be expended in pursuit of the study. Remember that risk is also a function of probability and if the target is difficult to attack or of no interest to a capable attacker the risk is proportionately lower. Risk assessment should follow international standards such as ISO 31000. The code recognises this as the unifying standard for security and safety. Communication between respective safety and security experts is critical and the interaction between their respective knowledge bases need to be workshopped and decisions recorded. When it comes to analysis, the code supports a qualitative rather than quantitative assessment on the premise this will gain more comprehensive support.
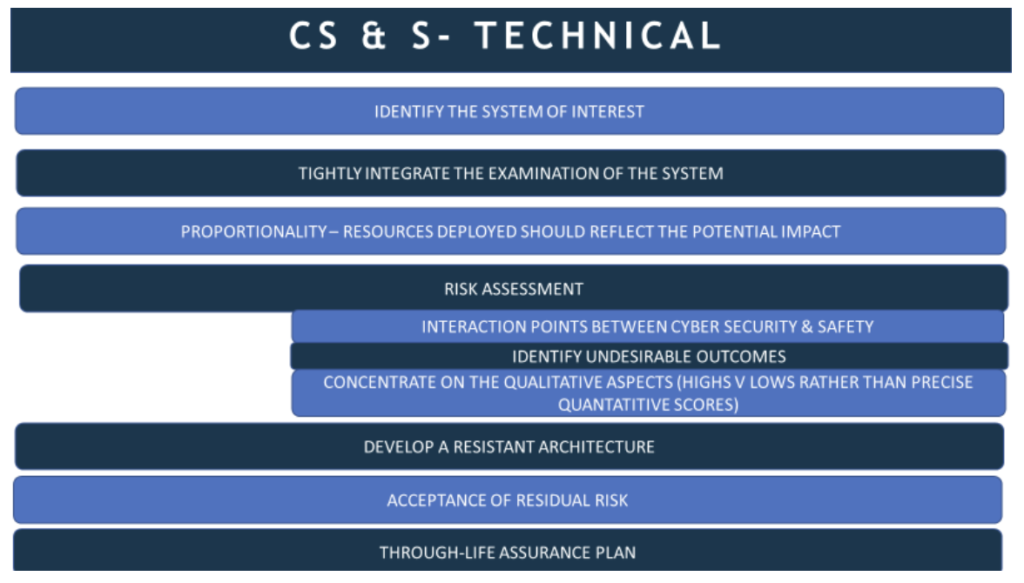
Identify and numerate the risks, then a more resilient architecture employing appropriate countermeasures and controls can be developed. Ensure those with senior responsibility apply resources to minimise residual risk, accept what can’t reasonably be eliminated, perhaps with added procedural management, and plan for future changes both in terms of functionality required as well as developing threat and attack patterns. On-going maintenance, patching, testing and incident procedures should be included in the assurance plan.
SWIFT Workshops
Risk assessment using Structured What IF Techniques (SWIFT) from ISO 27005 can be delivered through a series of workshops including key users and stakeholders. It is as relevant an exercise for safety as it is for IT or cyber security. Workshops must weigh up the context, the impact of compromise, and the probability of compromise. Taking into account the competence and motivation of attackers – those that would target national infrastructure such as the railway, allows us to estimate the threat. Workshops must examine vulnerabilities that might be exploited by such attackers. Findings should be documented and presented to senior management so they can decide whether to tolerate the risk or to treat it. How to treat risks can be presented formally to the business to demonstrate trade-offs between cyber security and safety. Business decisions will focus on and should optimise the return on Investment.
Accuracy and Relevance
Of course, this must include an accurate account of the cost of consequences if the identified risk is ignored. It must be convincingly relevant to the business, if not in monetary terms, in safety terms, in terms of reputation and legal obligation. Professional risk assessment should be coordinated by a senior information risk analyst, one approved and certified by the NCSC. Input from technical rail-orientated safety engineers, users and other stakeholders will be critical to mutual success. Above all, working in collaboration with information assurance professionals, solutions can be adopted that minimise risk within acceptable safety boundaries and where cyber security is addressed as a fundamental part of the safety paradigm – as part of the resilient safety strategy needed to take rail into the uncertain high-speed world of proliferating communications and reliance on interoperability. Assurance breeds confidence and it is that confidence the code of practice seeks to instil as rail moves forward. The prime objective of the code is to “help organisations responsible for safety related systems manage cyber security” – I hope this précis has helped.